Granular access with Row Level Security in Postgres
On my current side project I need user based granular access to provide access to 3 layers. I will not show everything here, but in short there are three layers where Layer 1 has children from layer 2, and Layer 2 has children from layer 3.
The access model I chose was to provide access by granting access explicit to each resource. So if you have layer 1 access you do not inherit access to the children, you have to explicitly get access.
Roughly like this: 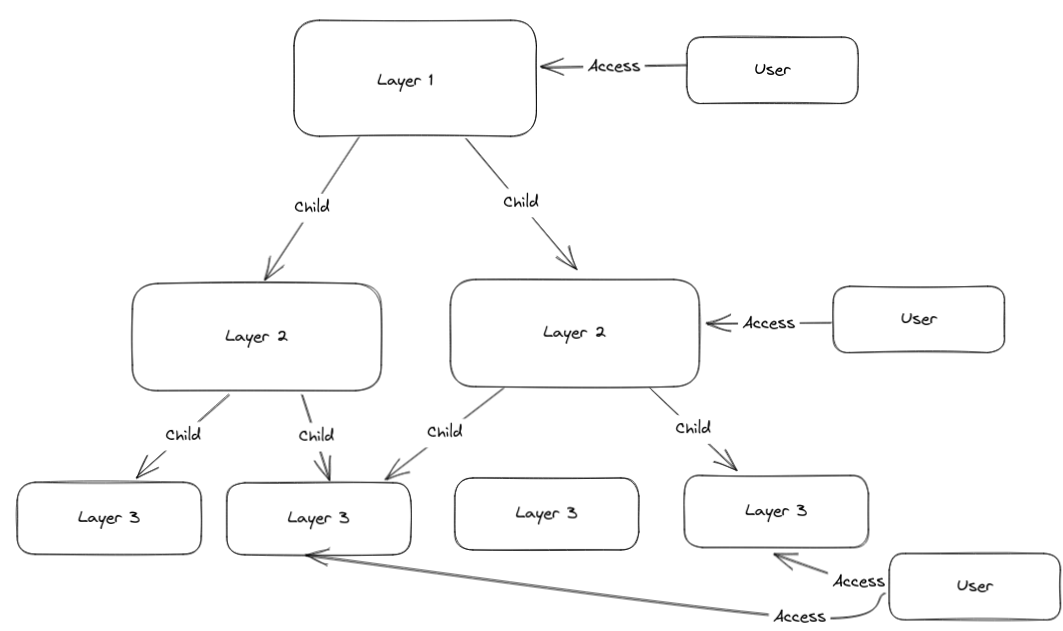
In my initial design I noticed that there wre a lot of repetitive WHERE statements which was might be easy to forget or prone to error (i.e WHERE user_id = X). So I explored other methods of doing the type of authorization I wanted and settled to use row level security which change the responsibility to database level.
I'm not really sure what I think about moving database logic to the database and not have it the data access layer (DAL). But in this case, the database and the DAL is strong coupled in a monorepo where I have full control over both.
Components
Example schema
The example schema will only have layer 1, since the complexity does not increase with more layers.
-- Table to store users
CREATE TABLE users (
user_id INT GENERATED BY DEFAULT AS IDENTITY PRIMARY KEY,
is_admin BOOLEAN NOT NULL DEFAULT FALSE
);
-- Table to store device information
CREATE TABLE devices (
device_id INT GENERATED BY DEFAULT AS IDENTITY PRIMARY KEY,
device_name TEXT NOT NULL,
);
-- Table to store the relationship between users and devices,
-- allowing each user to have access to multiple devices
-- Access level (0 = blocked, 1 = read, 2 = read-write, 3 = admin)
CREATE TABLE user_device (
user_id INTEGER REFERENCES users(user_id),
device_id INTEGER REFERENCES devices(device_id),
access_level INTEGER NOT NULL DEFAULT 0,
PRIMARY KEY (user_id, device_id)
);
Functions
-- The user who is executing the query
CREATE
FUNCTION current_app_user() RETURNS INTEGER AS $$ SELECT
NULLIF(
current_setting(
'app.current_user_id',
TRUE
),
''
) $$ LANGUAGE SQL SECURITY DEFINER;
-- Checks if a user is an admin
CREATE
FUNCTION is_user_admin(
_user_id INTEGER
) RETURNS BOOLEAN AS $$ SELECT
EXISTS(
SELECT
1
FROM
users
WHERE
user_id = _user_id
AND is_admin = TRUE
) $$ LANGUAGE SQL SECURITY DEFINER;
-- The function returns true if the user has a matching
-- record in the user_device table with access_level > _access_level
CREATE FUNCTION has_direct_access_to_device(_user_id INT, _access_level INT, _device_id INT)
RETURNS BOOLEAN AS $$
BEGIN
RETURN (
EXISTS (
SELECT 1 FROM user_device
WHERE user_device.user_id = _user_id
AND user_device.access_level >= _access_level
AND user_device.device_id = _device_id
)
);
END
$$ LANGUAGE plpgsql;
Make the table use RLS
-- DEVICE ROW LEVEL SECURITY
ALTER TABLE devices ENABLE ROW LEVEL SECURITY;
-- Allow access to the device table if the user has the
-- required access level, as determined by the has_access function
CREATE POLICY device_access ON devices
FOR SELECT
USING (
is_user_admin(current_app_user()) OR has_direct_access_to_device(current_app_user(), 1, device_id)
);
Queries
I'm writing my DAL in typescript and I use Slonik, a Node.js PostgreSQL client with strict types, detailed logging and assertions. A great library if you are comfortable with writing raw sql and do not want to use a query builder (like Knex.js) or an ORM (like prisma). Personally I've found that the complexity of learning different ORMs and query builders are about the same as just learning SQL but you get the advantage of it being language agnostic.
So back to the queries. The structure is simple:
- Start a transaction
- Set current user id localized to the current query
- Execute the query/queries
So the code looks something like this
-- app.current_user_id resets to original when the transaction ends
SET LOCAL app.current_user_id = X
await connection.transaction(async (transaction) => {
// extracted out to a helper function for consistency
await set_current_user_id(transaction, user_id)
devices = await transaction.many(
sql.type(deviceObject)`
SELECT DISTINCT d.device_id, device_name FROM devices as d
INNER JOIN user_device as ud
ON d.device_id = ud.device_id
WHERE device_id = ${device_id}
`
)
})
There is two major advantages to this structure
- I do not need to write
WHERE ud.access_level > X - I do not need to write JOINS on the access tables in the query, the result will always be what you have access to get.
References
I came across some great articles while implementing this that you can read for better context and explore other solutions.
